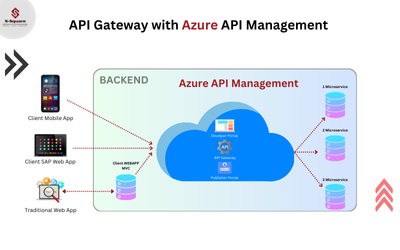
GnuPG is a GNU’s tool for secure communication and data storage and it’s a command line tool. Most companied that exchange sensitive data, such as payment details, employee information and so on over the internet use PGP encryption / decryption to transfer files securely.
Public and private keys play a key role in PGP to encrypt and decrypt the data. Public key is used to encrypt the data and is shared with end users. The private key is used to decrypt the data and is never shared with anyone.
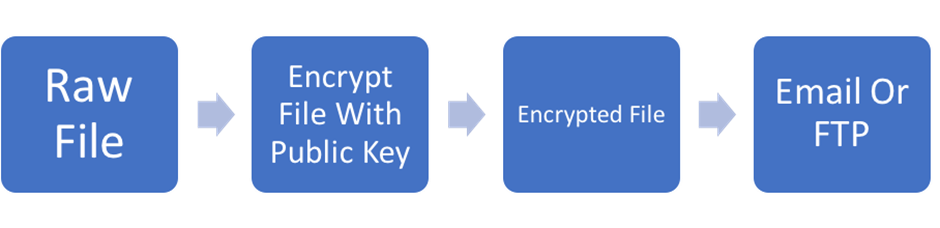
Steps to implement PGP:
-
- Need to have GnuPG package installed on Solaris / Unix servers
- Make sure package is in your PATH and able to access from anywhere in the server
- Generate KEY pairs using below command
Gpg –gen-key ——- After you run this command need to make sure follow below options
erpvisdb$ gpg –gen-key
gpg (GnuPG) 1.4.20; Copyright (C) 2015 Free Software Foundation, Inc.
This is free software: you are free to change and redistribute it.
There is NO WARRANTY, to the extent permitted by law.
Please select what kind of key you want:
(1) RSA and RSA (default)
(2) DSA and Elgamal
(3) DSA (sign only)
(4) RSA (sign only)
Your selection? 1
RSA keys may be between 1024 and 4096 bits long.
What keysize do you want? (2048)
Requested keysize is 2048 bits
Please specify how long the key should be valid.
0 = key does not expire
<n> = key expires in n days
<n>w = key expires in n weeks
<n>m = key expires in n months
<n>y = key expires in n years
Key is valid for? (0)
Key does not expire at all
Is this correct? (y/N) y
You need a user ID to identify your key; the software constructs the user ID
from the Real Name, Comment and Email Address in this form:
“Heinrich Heine (Der Dichter) <[email protected]>”
Real name: TEST PGP <[email protected] >
Invalid character in name
Real name: TEST PGP
Email address: [email protected]
Comment: testing
You selected this USER-ID:
“TEST PGP (testing) < [email protected] >”
Change (N)ame, (C)omment, (E)mail or (O)kay/(Q)uit? o
You need a Passphrase to protect your secret key.
We need to generate a lot of random bytes. It is a good idea to perform
some other action (type on the keyboard, move the mouse, utilize the
disks) during the prime generation; this gives the random number
generator a better chance to gain enough entropy.
……….+++++
…….+++++
We need to generate a lot of random bytes. It is a good idea to perform
some other action (type on the keyboard, move the mouse, utilize the
disks) during the prime generation; this gives the random number
generator a better chance to gain enough entropy.
.+++++
…..+++++
gpg: key FGRSBGYK marked as ultimately trusted
public and secret key created and signed.
gpg: checking the trustdb
gpg: 3 marginal(s) needed, 1 complete(s) needed, PGP trust model
gpg: depth: 0 valid: 3 signed: 0 trust: 0-, 0q, 0n, 0m, 0f, 3u
gpg: next trustdb check due at 2020-12-30
If you just want to Import Keys provided by Development Team using below command
-
- FTP the key files into server in one common location
- Import and sign the key files
erpvisdb$ gpg –import YourPrivateKey.asc
gpg: keyring `/usr2/applmgr/.gnupg/secring.gpg’ created
gpg: key ABCFRDSS: secret key imported
gpg: key ABCFRDSS: public key “XXXXXX_PGP < [email protected] >” imported
gpg: WARNING: key ABCFRDSS contains preferences for unavailable
algorithms on these user IDs:
gpg: “XXXXXX_PGP <[email protected] >”: preference for cipher algorithm 6
gpg: “XXXXXX_PGP <[email protected] >”: preference for cipher algorithm 5
gpg: “XXXXXX_PGP <[email protected] >”: preference for digest algorithm 5
gpg: it is strongly suggested that you update your preferences and
gpg: re-distribute this key to avoid potential algorithm mismatch problems
Set preference list to:
Cipher: AES256, AES192, AES, CAST5, 3DES, IDEA
Digest: SHA256, SHA1, SHA384, SHA512, SHA224
Compression: ZLIB, BZIP2, ZIP, Uncompressed
Features: MDC, Keyserver no-modify
Really update the preferences? (y/N) y
You need a passphrase to unlock the secret key for
user: “XXXXXX_PGP <[email protected] >”
1024-bit RSA key, ID ABCFRDSS, created 2019-02-20
Warning: using insecure memory!
gpg-agent [8280]: command get_passphrase failed: Permission denied
gpg: problem with the agent: Permission denied
gpg: update_keysig_packet failed: Operation cancelled
Key not changed so no update needed.
gpg: key ABCFRDSS: “XXXXXX _PGP <[email protected] >” not changed
gpg: Total number processed: 2
gpg: imported: 1 (RSA: 1)
gpg: unchanged: 1
gpg: secret keys read: 1
gpg: secret keys imported: 1
gpg –edit-key [email protected]
gpg (GnuPG) 2.0.29; Copyright (C) 2015 Free Software Foundation, Inc.
This is free software: you are free to change and redistribute it.
There is NO WARRANTY, to the extent permitted by law.
Secret key is available.
pub 1024R/ABCFRDSS created: 2019-02-20 expires: 2020-12-30 usage: SCEA
trust: unknown validity: unknown
sub 1024R/ABCDFERD created: 2019-02-20 expires: 2020-12-30 usage: SCEA
[ unknown] (1). XXXXXX_PGP <[email protected] >
gpg> trust
pub 1024R/ABCFRDSS created: 2019-02-20 expires: 2020-12-30 usage: SCEA
trust: unknown validity: unknown
sub 1024R/ABCDFERD created: 2019-02-20 expires: 2020-12-30 usage: SCEA
[ unknown] (1). XXXXXX PGP <[email protected] >
Please decide how far you trust this user to correctly verify other users’ keys
(by looking at passports, checking fingerprints from different sources, etc.)
1 = I don’t know or won’t say
2 = I do NOT trust
3 = I trust marginally
4 = I trust fully
5 = I trust ultimately
m = back to the main menu
Your decision? 5
Do you really want to set this key to ultimate trust? (y/N) y
pub 1024R/ABCFRDSS created: 2019-02-20 expires: 2020-12-30 usage: SCEA
trust: ultimate validity: unknown
sub 1024R/ABCDFERD created: 2019-02-20 expires: 2020-12-30 usage: SCEA
[ unknown] (1). XXXXXX_PGP <[email protected] >
Please note that the shown key validity is not necessarily correct
unless you restart the program.
gpg> sign
“XXXXXX_PGP <[email protected] >” was already signed by key ABCFRDSS
Nothing to sign with key ABCFRDSS
gpg>gpg> save
Key not changed so no update needed:
To see list of keys imported please used below command
gpg –list-keys
To Encrypt files, use below examples:
gpg -se -r “F2FD53A7” –no-tty –passphrase-file /usr2/.gnupg/XXX_Passphrase.txt –output XXX_test.pgp XXX_test.txt
erpvisdb$ gpg –passphrase ‘xxxx’ –output XXX_test.pgp –sign –encrypt -r ‘ ABCFRDSS’ omni_test.txt
To Decrypt files, use below examples:
gpg –output XXX_test.txt –decrypt XXX_test.pgp