As the business needs continue to increase the complexity of handling the data, lot of companies follow different ways to handle the threats which comes in the form of fishing, virus, data leaks or by hacking. Even though lot of security measures in place still lot of companies are facing issues with Data Loss and Data Breach. DLP software methodologies helps organizations in controlling these threats by following stringent compliance and process.
As of today, cloud usage is increasing to have high availability of the applications hence the threats are also increasing, and it is becoming hard to protect all kind of personal data to organizational data which spreads across the globe. DLP is more of a practice than a product, the process has to be continuously improved as we cannot protect everything by just installing any one of the DLP product.
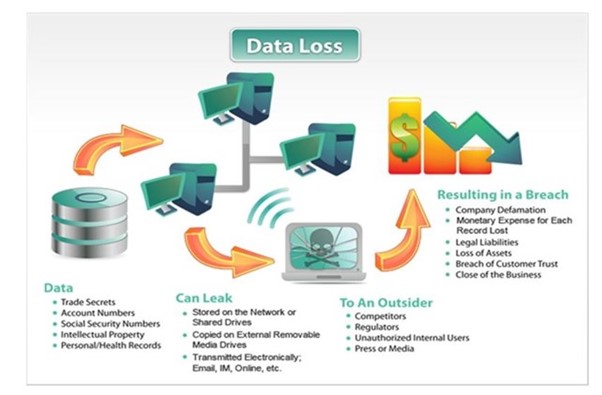
The above diagram gives a glimpse of how data loss or data breach can lead to damage at different levels and potential threats in an organization.
Lot of open source and light weight protocol supported DLP tools available in the market and these can be implemented to get started to understand the process and the efforts to eliminate or minimize these data losses especially with File Transfers from outside of the organization. These DLP products will have their individual databases with all latest virus signature details and will be updated on daily basis with the help of schedulers. Not only cyber threats, but physical threats can also be restricted with these DLP products.
These DLP software’s provide companies better strategy to control data access, file transfers, monitoring and reporting functions at all levels. Also, data transfer logs will play a crucial role in identifying how the data is being handled and alert notifications will help in identifying or minimize the damage. Most of the companies will need these data logs for audit purpose and these logs will be stored for years to analyse and improve the process of data handling.
Organizations find it easy to identify the risks beforehand, fix them in time and find ways to prevent them from re-occurring by following the DLP process. Also, DLP helps in centralizing the monitoring while decentralizing the security, that means keeping more security check at different levels for better risk-free environment.
Organization’s network communications “File Transfer Protocol, Web Applications, email exchange which uses HTTP, HTTPS, FTP, FTPS, TCP/IP protocols” can be monitored and the traffic can be controlled while enabling SSL. Each and every file or message coming into or going out of the organization’s network can be scanned and compared with existing database of virus threats and then only allowed to transfer. Also, DLP solutions also need to follow regulatory compliance requirements to follow the standards.
Some of the DLP architectural components which can be used to make the most of process implementation.
Network Monitoring
Email Integration
Proxy integration
Internal Networks
Content Discovery Techniques
Endpoint limitations
Directory Integration
Role-Based Administration
Hierarchical Management
Most of the Anti-Virus software companies also deal with DLP software products and each one of them will have different features that can be customized as per the client needs and can be deployed and monitored easily.
To name a few industry standard DLP software products:
McAfee DLP EndPoint
Symantec EndPoint DLP
SecureTrust DLP
Teramind DLP
CheckPoint DLP